8 minutes
Cyber Threat Hunting - Leveraging the Kill Chain
Cyber Threat Hunting is a critical component necessary to ensuring comprehensive defense and response measures are in place by taking a proactive approach to detecting threats. While threat hunting itself is not a new concept, the actual execution of it is constantly evolving. The current inception of threat hunting is enabled by the fact that big data handling has become more feasible along with the advent of advanced statistical analysis and machine learning.
There are many frameworks and methodologies that have been created around modern cyber threat hunting. Some of these particular implementations are specialized for specific environments, circumstances, or data sources, while others are more generic, applicable across any situation. The one thing which the majority of these methodologies have in common however, is the fact that they all leverage or reference an attacker lifecycle in some way.
There are many considerations and components which should be accounted for while preparing to execute a hunting mission, but a few of those include the following:
The Attacker Lifecycle The Cyber Kill Chain is an industry-wide de facto standard for modeling threats within the cyber ecosystem. The Kill Chain was originally created by several researchers at the Lockheed Martin Corporation as part of a methodology to more appropriately model and defend against increasingly advanced adversaries. The primary benefit of approaching defensive cyber operations from the perspective of the Kill Chain is a disciplined framework to focus and scope intelligence-driven defensive operations such as cyber threat hunting.
Defining Normality in Organizations It is just as important to assess and understand your own organization as it is profiling and understanding the enemy. This is one of the most common things that companies tend to struggle with. Inventory of assets, criticality of data, normal business to business (B2B) communications, etc. Fully understanding and awareness of these things makes defending (and proactively hunting) much more successful.
Intelligence-Driven This may be the most important factor within the entire threat hunting process. While the full details of how to execute this will be documented in a subsequent post, it is critical to understand that intelligence will not only scope the hunting process, but also provide relevance to any findings within the context of the attacker lifecycle.
Scoping Hunt Missions
The Cyber Kill Chain is broken down into the following categories:
- Reconnaissance
- Weaponization
- Delivery
- Exploitation
- Installation
- Command & Control (C2)
- Actions on Objectives
Many organizations with access to large amounts of data which they can hunt through will conduct both targeted and generic hunts. The kill chain is leveraged through both approaches.
With targeted hunting, the pre-defined scope of potential adversaries and their historically attributable tactics, techniques, and procedures (TTPs) are taken into account and broken out to the respective category which they fall under in the Cyber Kill Chain. This then allows analysts to focus on appropriate data sources necessary for locating Indicators of Compromise (IOC), Indicators of Activity (IOA), or anything else of relevance.
With regard to generic hunting, analysts can appropriately scope the focus of individual hunt missions based on the categories of the Cyber Kill Chain. Under this method, analyst can start hunting very broadly within the chosen category, making a series of pivots on the data returned, until it reaches a manageable size for the analyst to peruse through, line by line. Should any indicators or suspicious items be found, analysts can then shift the focus laterally across the Cyber Kill Chain to establish more evidence of an attack or escalate to a senior analyst to carry out the investigation.
The best way to understand the advantage of leveraging the kill chain for hunting is to see an example of it in action.
The Hunt
First, we must determine our data sources relevant to the hunt. In this case, system logs, security event data, and host level information are available. The advantage of having multiple sources of data, such as an MSSP with multiple customers, is an expanded, diverse data set for which to make comparisons. While this adds some complications in baselining, it significantly increases the value of the data set for comparative analysis to identify suspicious activity based on anomalies.
Under generic hunting, we can choose to look for specific identifiers within the respective category chosen, look for anomalies within the larger data set, or a combination of the two. Additionally, we must determine the window of time to focus on. For generic hunting, these missions are usually executed on cyclical rotations, ensuring activity from any given time gets coverage. Anomaly based generic hunting requires multiple successive pivots to systematically filter out more and more data, so for simplicity, we will focus on hunting for specific identifiers. Although this method also relies on successive pivots, it is much easier to demonstrate.
Two short example hunt missions are explored below.
Example # 1 – Actions on Objectives (Privilege Escalation) via net Command Usage
For this example we will explore a generic cyber threat hunt mission, focused on identifying activity categorized within the actions on objectives phase.
For this search we are limiting to a single customer, looking for all process creation events executing the net command
within the last 24 hours:
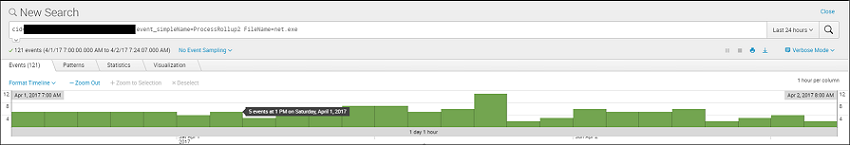
The search has returned 121 results. While this is surely a manageable number of events for an analyst to investigate, we can clear them out even further by filtering out normal activity based on established baselines:
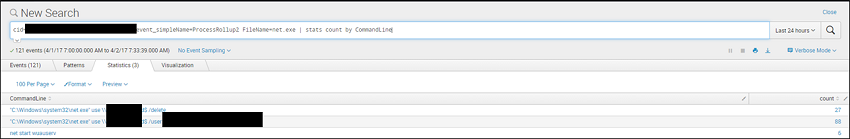
We can see that, across the customer’s entire environment, the 121 events are comprised of only 3 unique commands. Breaking this our further by individual system reveals even more insight:
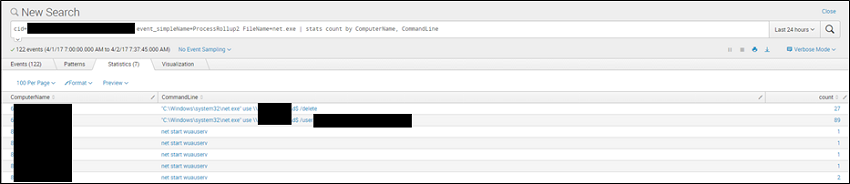
Based on previously documented baselines and defining normality for this customer, we can determine that the wuauserv
activity (Windows update automatic update service) is expected activity and rule it out. We can dig further into the
net use commands:
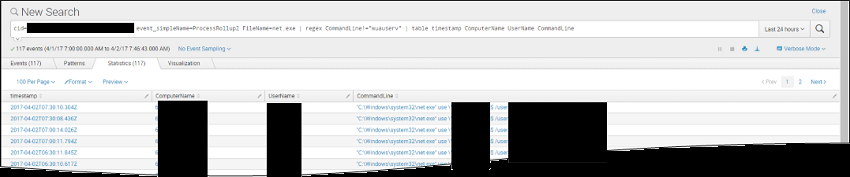
The results (truncated for brevity) reveal the activity within the context of time. We can then compare this activity with the normal, expected activity within the respective systems (either by comparing to baselines or verifying with the customer).
If there were any suspicious results which could not be accounted for as legitimate, the next step would have been to paint additional context around it, such as by seeing what else the user is executing shortly before and after; what other processes are being run; and parent-child process relationships. Identified suspicious activity can then be compared to other data sources to enrich these findings and then to shift focus across the Cyber Kill Chain categories for extending context.
Example # 2 Exploitation Leveraging a Software Vulnerability (CVE-2017-5638)
For this next example, we will explore how finding anomalies in the data set can reveal malicious activity (or attempts). In this search, we are searching for event data to identify all unique request and response HTTP headers. We will not restrict to a single customer in this case in order to encompass a larger, diversified data set:
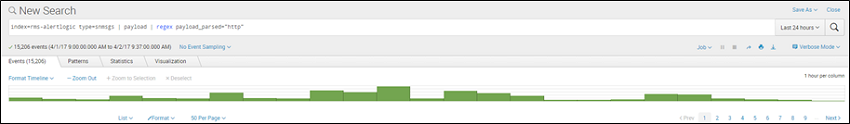
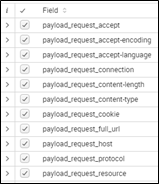
The (partial) list of results shows that it has captured over 50 unique HTTP headers. We can then look for certain outliers in the respective headers such as significantly higher or lower occurrences of a value or even significant differences in the length of the values themselves.
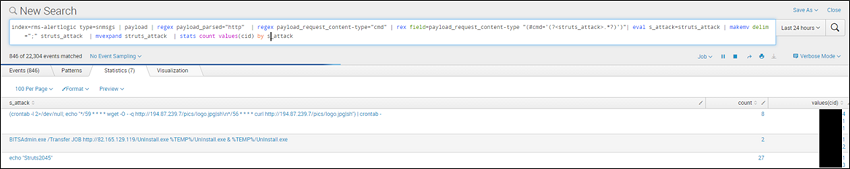
As we browse through the top values of each result, we discover an interesting finding within the request packet’s content-type header. Not only are there two entries far longer than the rest, but one also has a very high rate of occurrence.
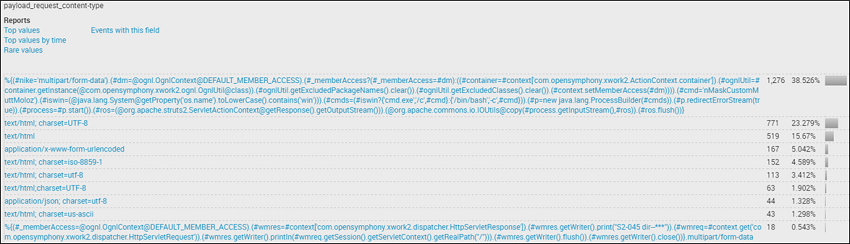
We can further verify how much of an outlier this truly might be by examining all unique values. This reveals that there are some repeating patterns within the value itself. A review of the RFC will reveal that this is not expected activity. Of course we now know that this is the attempted exploitation of CVE-2017-5638, targeting Apache Struts, but this process shows how this activity might have been detected prior to its discovery and disclosure.
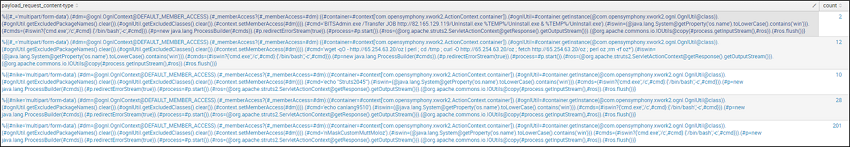
We can now make a pivot on this data to extract all of the attempted malicious command line activity by targeted customer within the Apache Struts vulnerability, so we can then search our host level data for verification that the commands were not successfully executed.
Conclusion
Cyber threat hunting is critical to effectively identifying potential threats or compromises by taking a proactive approach. There are many different methodologies and techniques to guide cyber hunt missions, but the right one should be dictated by specific circumstances. Regardless of how it is executed, examining the environment through the attacker lifecycle will help guide scope and provide additional insight which might not have been considered.
Taking a proactive approach to securing and detecting malicious activity within your environment is paramount in today’s technologically dependent landscape. Hunting through an attacker lifecycle or the Cyber Kill Chain will allow you to identify and stop threats which traditional signature-based methods might miss.
originally posted on a previous blog of mine
update: this was also released, in a shorter, modified version at this blog here as well as this white paper